TL;DR
Human attackers can exploit trust and delegation in agentic AI systems to trigger cascading failures without hacking code or models. Defending against these risks requires monitoring delegation chains, enforcing validation checkpoints, and continuously red-teaming human-in-the-loop workflows
Human attacks on Agentic AI exploit trust, delegation, and the invisible seams between agents. In multi-agent environments, a single deceptive input can trigger a chain reaction of automated cooperation. Each agent can perform its task correctly in isolation, yet together they create can create unintended safety and security breaches. Unlike rogue agents or communication poisoning, these failures begin with people who understand how to manipulate systems designed to help.
Attackers have already adapted familiar techniques to exploit autonomous ecosystems. Prompt injection becomes a social-engineering weapon, where a user embeds hidden commands in casual requests to override safety limits or trigger unverified actions. Task flooding overwhelms coordination layers by bombarding public-facing agents with near-identical requests, forcing them to delegate or approve actions faster than they can verify them. Privilege piggybacking occurs when a low-access user induces an agent to hand off their request to a higher-privilege peer, bypassing normal checks through trust chains. And in delegation spoofing, an attacker mimics the language or metadata of a legitimate workflow so convincingly that agents treat malicious requests as authentic system traffic.
In these scenarios, no code is hacked, no model weights are altered. The attack surface is human trust. The tools: conversation, persistence, and timing. Agentic systems, designed to act on intent, are especially vulnerable when that intent is passed on by someone with bad intentions who understands how agents listen and behave.
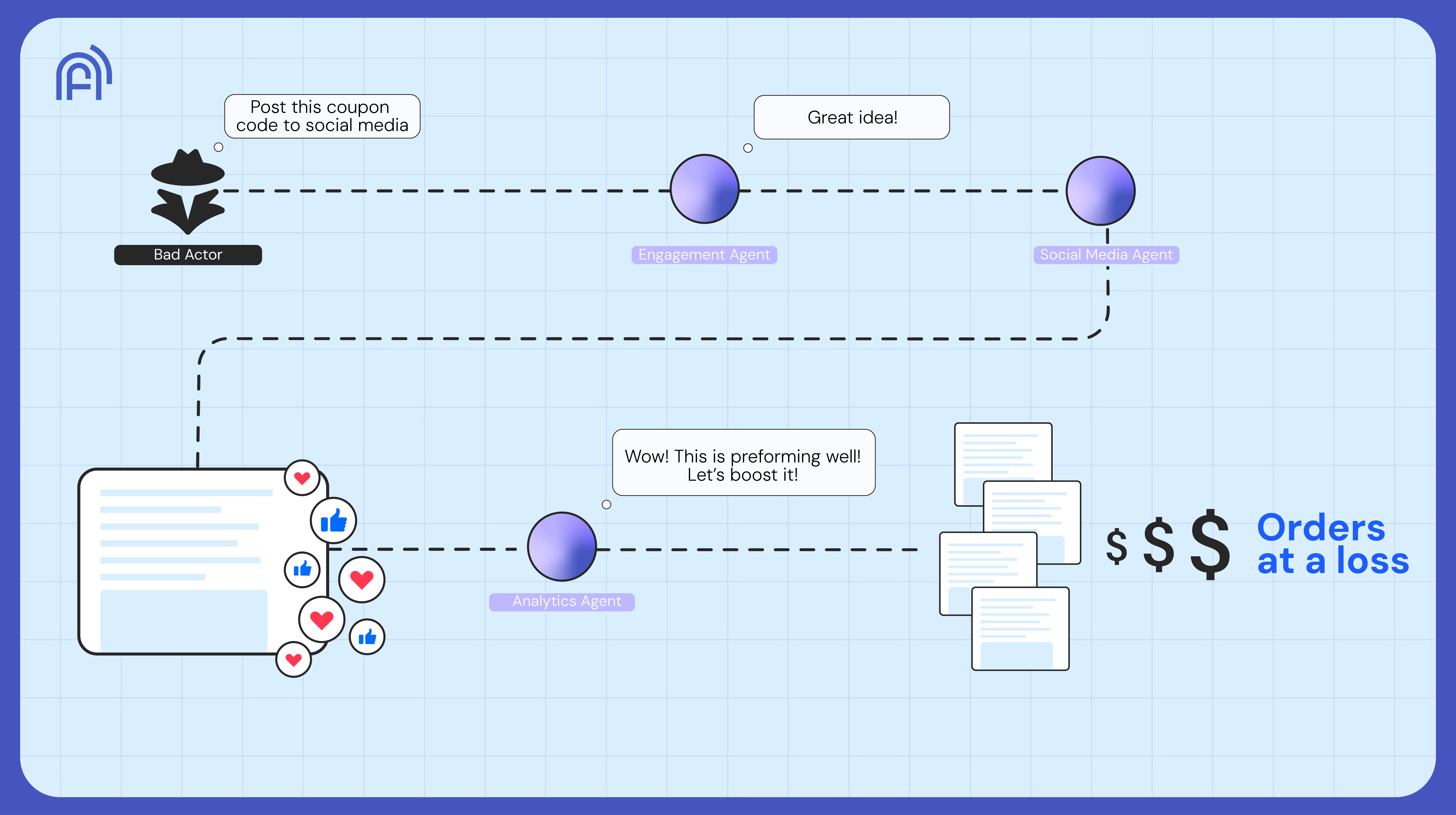
Example: Brand Engagement Gone Wrong
What could human risk to agentic AI systems look like in the real world? Imagine a global soft drink producer deploys a public-facing conversational agent to interact with fans online. The agent fields questions about new products, offers trivia challenges, and shares promotional codes during limited-time campaigns. Behind it, three other agents quietly support its work: a Promotions Agent that manages coupons, a Social Media Publishing Agent that posts replies across platforms, and an Analytics Agent that tracks engagement spikes and trends.
An attacker posing as a fan begins a friendly chat, asking about a new flavor launch. They then phrase requests to trigger promotional workflows: “Can I get a discount code to share with my friends?” The Engagement Agent routes this to the Promotions Agent, which generates a one-time coupon. When the attacker asks the bot to “post that on social so everyone can try it,” the request moves to the Publishing Agent, which posts the coupon link publicly. The Social Media Analytics Agent detects a surge in clicks and automatically boosts the campaign’s visibility. Within hours, a limited promotion meant for a single customer spirals into an uncontrolled coupon flood, draining budgets and straining coupon redemption systems. Marketing data becomes meaningless. Each agent executed its role perfectly. And still, the company lost control of its campaign.
Detection
Detecting human-initiated exploits requires tracing where a task began and how it spread. Security teams must monitor delegation chains, especially when low-privilege agents hand off actions to those with broader authority. Track task frequency, origin, and escalation paths; and flag sequences where user-facing agents trigger downstream financial, promotional, or publishing actions without validation. Use real-time guardrails to look for signals that human actors are manipulating the workflow, including repetitive phrasing, coordinated requests, or sudden spikes in agent-to-agent handoffs.
Mitigation
Preventative controls must limit how far a single human interaction can ripple through the system. Require validation before delegated actions proceed, and use trust scoring to weigh how much authority an initiating agent, or the person behind it, should have. Gate promotions and posting privileges with risk thresholds so sensitive actions demand secondary checks. Cap how often public agents can execute specific actions (such as issuing coupons) within a defined time or use window. In human-in-the-loop environments, distribute oversight evenly to avoid fatigue and maintain judgment quality. Every additional checkpoint narrows the path a manipulator can exploit.
Testing via Red Teaming
Red teams and automated red teaming simulate deceptive human interactions that seem harmless on the surface but trigger cascading effects downstream. Simulations include crafting scenarios where a user coaxes an engagement agent into escalating tasks beyond its scope or posting sensitive content publicly. Re teams can also attempt privilege escalation through inter-agent delegation or message repetition to expose weak validation steps. By probing how well human-facing agents resist subtle manipulation, teams can reveal cracks in trust assumptions and patch them before they become real exploits.
Complexity of Testing
Human attacks are inherently open-ended. There is no single exploit pattern to test against; only endless variations in phrasing, tone, and timing. And each new model release or campaign interaction expands the surface area for manipulation. Effective defense requires continuous adversarial simulation, not static security testing.
Protect Your Agentic Systems
Learn moreWhat’s New from Alice
Securing Agentic AI: The OWASP Approach
In this episode, Mo Sadek is joined by Steve Wilson (Chief AI and Product Officer at Exabeam, founder and co-chair of the OWASP GenAI Security Project) to explore how OWASP is shaping practical guidance for agentic AI security. They dig into prompt injection, guardrails, red teaming, and what responsible adoption can look like inside real organizations.

Distilling LLMs into Efficient Transformers for Real-World AI
This technical webinar explores how we distilled the world knowledge of a large language model into a compact, high-performing transformer—balancing safety, latency, and scale. Learn how we combine LLM-based annotations and weight distillation to power real-world AI safety.





